Improving Authentication:
Our lab designs authentication schemes to take advantage of users’ natural cognitive abilities. This approach requires understanding how authentication interactions can be improved by translating our knowledge of human capabilities to the design of authentication schemes. Our efforts have resulted in innovative graphical authentication prototypes (e.g., Cain & Still, 2017; Tiller, Angelini, Leibner, & Still, 2019) and their associated provisional patents. To bridge the gap between research and practice, we have provided a list of authentication design guidelines (Still, Cain, & Schuster, 2017) and consolidated the recognized usability issues into usability strengths/weaknesses (Cain & Still, 2018; Cain & Still, under review; Mator, et al., 2020). In addition, we have started to explore the over-the-shoulder-attack vector from a behavioral perspective (e.g., Cain, Werner, & Still, 2017; Cain, Chiu, Santiago, & Still, 2016), which is a recognized weakness of next-gen graphical authentication. We examined the impact authentication schemes have on our limited working memory resources (Still & Cain, 2019; Mator & Still, 2025; Notepad LM Podcast). Recently, we have been exploring how the Cognition-Inspired Design approach is crucial for the effective development of next-generation authentication systems (Still & Still, 2025).
Listen to our Human-Centered Security Podcast Episode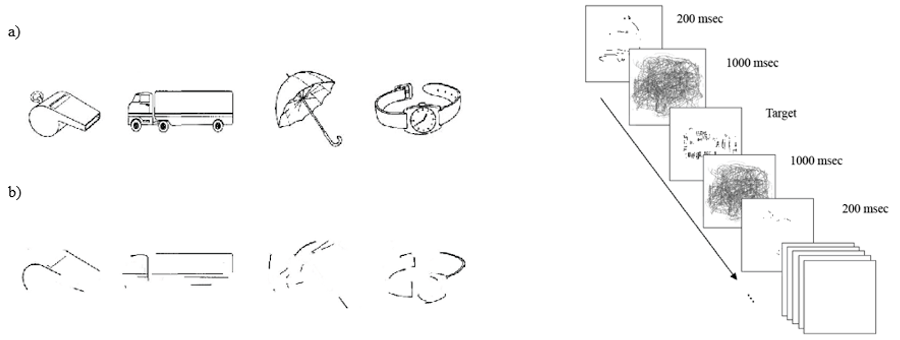
Image taken from Cain and Still (2017). Rapid, Serial, Visual Presentation method (RSVP) authentication scheme, which presents users with a stream of rapid, degraded images. RSVP is easy for end-users but difficult for casual over-the-shoulder attackers. Pane A shows the passcode objects and Pane B shows them degraded.
